Android Aslr Bypass Best of 2021
Their implementation involves the exploitation of the CVE-2015-3864 and the Address Space Layout Randomisation ASLR bypass. An animation illustrating the end-to-end process of a remote ASLR bypass is shown below.
Cs 519419 Cyber Attacks Defense Address Space Layout
So should you be worried.

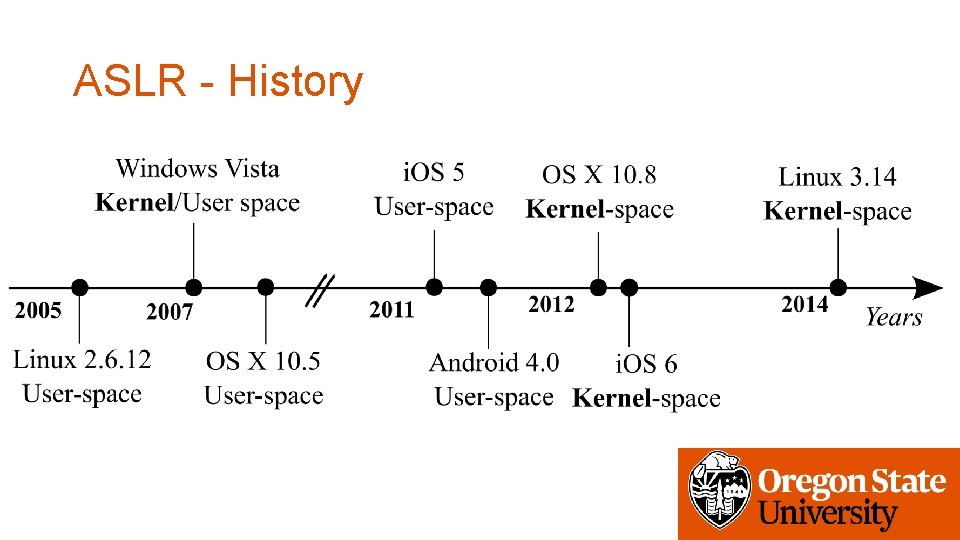
Android aslr bypass. We identify not only local but also remote attack vectors which obviate the common need for a pre-installed app to carry out attacks on Android devices. One of the most significant and scary parts about Metaphor is its ability to affect a large percentage of Android devices. The current versions of all major operating systems iOS Android Windows macOS and Linux feature ASLR protection.
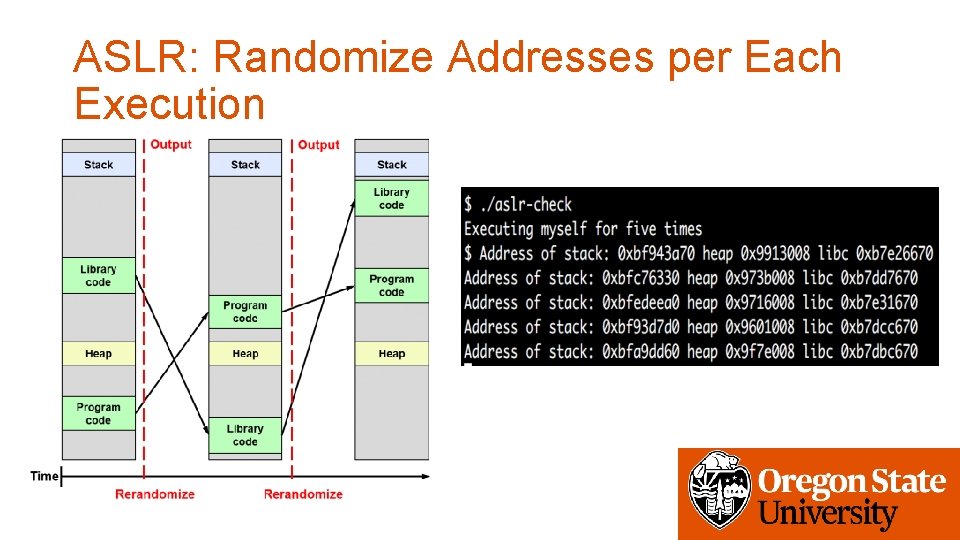
This is a situation where a value on the stack at a reliable location might be used to locate a usable function pointer or ROP gadget. For a detailed description of ASRL implementation in Linux see 2. Bypass SELinux on Android.
Certain vulnerabilities allow attackers to obtain the addresses required for an attack which enables bypassing ASLR 3. Once this is done it is sometimes possible to create a payload that reliably bypasses both protection mechanisms. Does anyone have an idea how to bypass the ASLR here without leak address.
As well as my binary contains a call to system so I can jump to system but in this case I need to put the address of string in R0 but no possible since the ASLR. But in the past week a new method of bypassing ASLR has been found. ASLR is a technology used to stop shellcode from being successfully executed.
The only way to reliably bypass DEP and ASLR is through an pointer leak. Rumors say it that some entities around the world managed to do it but AFAIK nobody published anything as they might use it for gathering intelligence. Zusätzlichen Schutz bietet die Adress Space Layout Randomization ASLR aber auch diese Schutzmaßnahme lässt sich natürlich umgehen.
Its worth noting that the animation depicts the exact same queries that were made in the original exploit demo recorded in April so its based on the slightly slower algorithm 2. The PoC includes lookup tables for Nexus 5 Build LRX22C with Android 501. The source include a PoC that generates MP4 exploits in real-time and bypassing ASLR.
Exploiting Android Stagefright with ASLR Bypass Everybody knows that exploiting remote code execution vulnerabilities is a real challenge. How To Impress Girls With Browser Memory Protection Bypasses. The usermode audio subsystem for the Samsung Android Professional Audio is based on JACK which appears to be designed for single-user usage.
ARM and Thumb Instruction Set. Bypassing ASLR and DEP – Getting Shells with pwntools. The PoC includes lookup tables for Nexus 5 Build LRX22C with Android 501.
Samsung Android JACK ASLR Bypass Posted Jul 6 2016 Authored by Google Security Research Mark Brand. Universal DEPASLR bypass with msvcr71dll and monapy Published July 3 2011 By Peter Van Eeckhoutte corelanc0d3r Over the last few weeks there has been some commotion about a universal DEPASLR bypass routine using ROP gadgets from msvcr71dll written by Immunity Inc and the fact that it might have been copied into an exploit submitted to Metasploit as part of the Metasploit bounty. I am able to override as well 4 registers.
It was claimed the bug was impractical to exploit in the wild mainly due to the implementation of exploit mitigations in newer Android versions specifically ASLR the paper states. The attack page is indexphp. Metaphors source code is now released.
Server-side of the PoC include simple PHP scripts that run the exploit generator – Im using XAMPP to serve gzipped MP4 files. I use his TinyInjector as a basis and I extend one to the Android 80 realms particularly to the ARM64 architecture original version supports 32-bit ARM SELinux and the linker namespace. The source include a PoC that generates MP4 exploits in real-time and bypassing ASLR.
8 Zeilen The source include a PoC that generates MP4 exploits in real-time and bypassing ASLR. Address Space Layout Randomization ASLR is a security technique used in operating systems first implemented in 2001. Today Id like to take some time and to present a short trick to bypass both ASLR Address Space Layout Randomization and DEP Data Execution Prevention in order to obtain a shell in a buffer-overflow vulnerable binary.
Since the appearance of ASLR attackers have invented various methods of bypassing it including. Enable attackers to easily bypass ASLR exposing Android apps to critical attacks such as return-oriented programming ROP. By launching attacks at popular apps including the Chrome browser and.
The team here at North-Bit has built a working exploit affecting Android versions 22 to 40 and 50 to 51 while bypassing ASLR on versions 50 to 51 as Android versions 22 to 40 do not implement ASLR. Server-side of the PoC include simple PHP scripts that run the exploit generator – Im using XAMPP to serve gzipped MP4 files. Shared Library Injection in Android ASLR bypass is there as well.
Angriffe trotz ASLR Eine Reihe von Möglichkeiten zum Umgehen von ASLR wurden auf der Sicherheitskonferenz Black Hat USA 2008 von Alexander Sotirov und Mark Dowd beschrieben. Needless to say any ASLR bypass logic we devise will most likely assume 100 accuracy of the oracle output so we have to put some. This generally holds true but we have no guarantee that the condition will be always met especially since the relevant jemalloc bin chunks between 129-160 bytes in size is not particularly quiet and is also utilized for other unrelated objects by the Samsung Messages app.

Pdf Aslr And Rop Attack Mitigations For Arm Based Android Devices

Cs 519419 Cyber Attacks Defense Address Space Layout

A Simple Javascript Exploit Bypasses Aslr Protection On 22 Cpu Architectures

Pdf Aslr And Rop Attack Mitigations For Arm Based Android Devices

Cs 519419 Cyber Attacks Defense Address Space Layout

Mms Exploit Part 4 Mms Primer Completing The Aslr Oracle Laptrinhx

Android 32 Bit Aslr Too Weak To Block Stagefright Exploits Says Google Researcher Tom S Hardware

A Simple Javascript Exploit Bypasses Aslr Protection On 22 Cpu Architectures

Pdf Aslr And Rop Attack Mitigations For Arm Based Android Devices

Novel Aslr Bypass Depends On Cpu Hardware
Aslra Summary Of Pax Aslr In A 32 Bit System Download Scientific Diagram

Aslr Bypass Techniques Are Popular With Apt Attacks
Cs 519419 Cyber Attacks Defense Address Space Layout

Aslray Linux Elf X32 And X64 Aslr Bypass Exploit With Stack Spraying Pentesttools

Metaphor Exploit A Follow Up To Stagefright That Puts Millions Of Android Devices At Risk
Shared Library Injection On Android 8 0
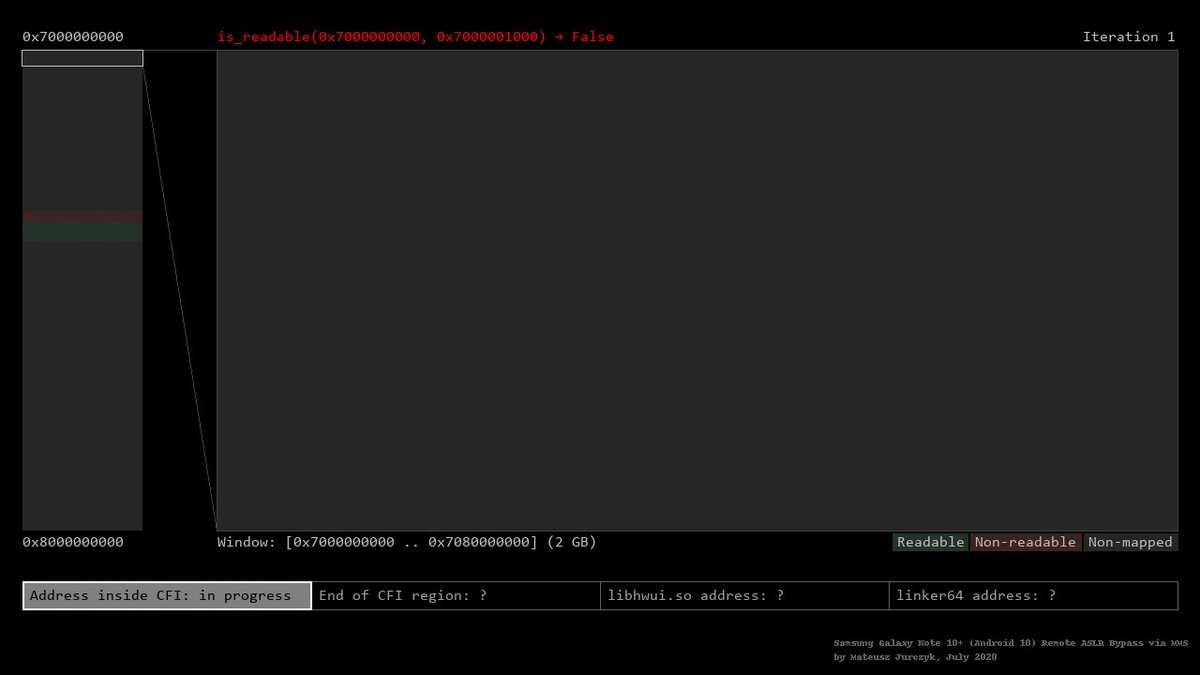
J00ru Vx On Twitter A Direct Link To The Exploit Is Here Https T Co Bzxsjas5uj And A Visualization Of The Aslr Bypass 3 Mentioned In The Post Is Shown In The Gif Below Relevant Frames


Post a Comment for "Android Aslr Bypass Best of 2021"